A wireless LAN can be deployed in many ways, depending on the architecture it is built on. There are many wireless devices available today, so it is best to choose devices that interoperate when building a wireless LAN.
This article explains wireless LAN hardware, including wireless network adapters and access points. We discuss their configuration and the standards they follow.
Wireless LAN Adapters
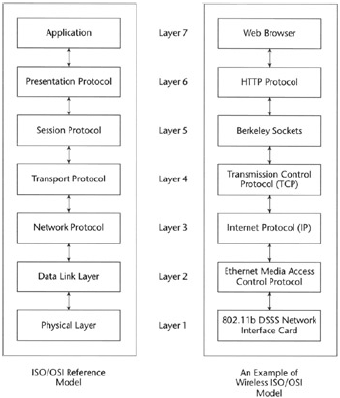
Each and every computer in a wireless LAN must have a wireless network adapter. Having this device in place and in operation ensures that the different computers' OSI models will be compatible with one another. Figure1 shows an OSI Reference Model for a generic wireless LAN.
For our concerns with wireless networks, we need only reexamine the bottom two layers of the model—the physical layer and the data−link layer—as there is some variation here between the wireless and nonwired networks.
For any given implementation the higher layers do not differ appreciably between the two kinds of networks.
Wireless LAN adapters (network interface cards) implement the physical layer of the OSI Model and conform to the data−link layer to provide proper media access control (MAC)−level interface.
The Physical Layer
The primary difference between a wireless LAN adapter and a wired LAN adapter is its physical layer.
The physical layer in wireless adapters does two things: When data is transmitted, it converts the electronic signals into medium−dependent signals, and when signals are received from the medium, it converts them into electronic signals for higher layers to interpret.
How well a wireless network is going to perform depends on the bandwidth of the electromagnetic spectrum, the quality of the components that make up the network adapter, and the protocols used.
For electrical signals (such as those used in cordless phones, FM radio, and wireless LANs) to propagate through the air, they must be converted into electromagnetic waves.
An electromagnetic wave is energy that travels and spreads out as it goes—for example, visible light that comes from a lamp in your house or radio waves that come from a radio station.
The distance that an electromagnetic wave can travel depends on its wave properties. These properties include the wavelength and the frequency of an electromagnetic wave.
Scientists and industry standard committees have divided and named different types of electromagnetic waves into bands based on their properties (see Figure 2).
Each electromagnetic band has a certain minimum frequency and a maximum frequency, and all the radiation that falls between the two is known as the band frequency.
The entire set of known electromagnetic waves is called the electromagnetic spectrum.
Examples of electromagnetic waves are radio frequencies (RF), microwaves, infrared and ultraviolet light, X−rays, and gamma rays.
Due to the highly popular nature of wireless connectivity and the limited availability of the electromagnetic spectrum, wireless LANs use a limited bandwidth of the electromagnetic spectrum to transmit data over the ether or air.
Today, there are three basic electromagnetic spectrum bands that are commonly used for data transmission over wireless LAN links: infrared, radio frequency, and microwave.
Infrared
Infrared−based systems are the simplest and least expensive wireless LANs. These systems work best when operated in the line of sight (that is, the transceivers involved in communication must face one another without any physical obstruction).
Infrared systems are not bandwidth constrained—in other words, the signal does not spread, so devices using infrared can use the entire bandwidth of infrared when communicating with one another without any interference with any other device. They also can attain high speeds at relatively low costs compared to other competing types of systems.
Another benefit of using an infrared−based system is that it does not require any licensing from the Federal Communications Commission (FCC), which only regulates the RF portion of the electromagnetic radiation between 9 kHz and 300 GHz.
Infrared radiation falls in the light portion of the electromagnetic spectrum that is not regulated by the federal government. A precisely aimed infrared system can attain a high range, up to several miles, which can be good for internetworking.
However, when you need omni−directional connectivity, where the signals are bounced off nearby objects in all directions, system performance is reduced. Infrared systems do not perform well under such conditions.
Infrared systems also suffer from interference from sunlight and artificial light. Initially, infrared systems were very popular, but their unreliability due to easily obstructed signals means these systems have limited use.
Microwave
Microwave (MW)−based networks normally operate in the 5.8−GHz band and use less than 500 milliwatts of power. The typical range for a microwave−based system in a closed office environment is about 120 feet.
The big advantage to MW systems is higher throughput, as MW systems do not have the overhead involved with spread spectrum systems. MW−based adapters are normally used in commercial settings.
Radio
Radio frequency (RF)−based wireless LANs are by far the most popular wireless LANs in the United States. FCC regulations require that RF systems use spread spectrum technology (see Figure 3). Spread spectrum modulation techniques are defined as being those techniques in which the following occur:
- The bandwidth of the transmitted signal is much greater than the bandwidth of the original message.
- The bandwidth of the transmitted signal is determined by the message to be transmitted and by an additional signal known as the spreading code.
Spread spectrum was originally designed for the U.S. Navy to hide the signals that controlled torpedoes. The topic was classified for years by the U.S. military, and only recently were the patents made public.
Systems that use spread spectrum must use the exact same frequency and related parameters. These parameters are defined by a particular implementation of spread spectrum technology. The commonly used RF bands in most countries for wireless LANs are 2.4 GHz and 5.x GHz (the x in 5.x varies).
Currently two types of spread spectrum technology exist: direct−sequence spread spectrum (DSSS) and frequency−hopping spread spectrum (FHSS). Because the signal does not stay in one place on the band, FHSS can elude radio interference.
DSSS avoids interference by configuring the spreading function in the receiver to concentrate the desired signal and spread out and dilute any interfering signal.
There is a lot of overhead involved with spread spectrum, and so most of the DSSS and FHSS systems historically have lower data rates than infrared− or microwave−based systems.
- Direct−sequence spread spectrum (DSSS). In the direct−sequence spread spectrum (DSSS), the transmission signal is spread over an allowed band (see Figure 4).
The data is transmitted by first modulating a random binary string called spreading code on the carrier wave (the chosen electromagnetic frequency). The data bits are mapped to a pattern of ratios of spreading code bits called chips and mapped back into bits at the destination.
Looking at it another way, the number of chips that represent a bit is the spreading ratio. The higher the spreading ratio, the more the signal is resistant to interference. The lower the spreading ratio, the more bandwidth is available to the user.
The FCC mandates that the spreading ratio must be more than 10. Most products have a spreading ratio of less than 20. The transmitter and the receiver must be synchronized with the same spreading code. If orthogonal spreading codes are used, then more than one LAN can share the same band.
However, because DSSS systems use wide subchannels, the number of colocated LANs is limited by the size of those subchannels. Recovery is faster in DSSS systems because of the ability to spread the signal over a wider band.
- Frequency−hopping spread spectrum (FHSS). This spread spectrum technique divides the frequency band into smaller subchannels of usually 1 MHz (see Figure 5).
For example, in most wireless LANs the 2.4−GHz band is divided into 11 1−MHz subchannels. The transmitter then hops (switches) between the subchannels, sending out short bursts of data for a given time.
The maximum amount of time that a transmitter spends in a subchannel is called the dwell time. In order for FHSS to work correctly, both communicating ends must be synchronized (that is, both sides must use the same hopping pattern); otherwise they lose the data.
FHSS is more resistant to interference because of its hopping nature. The FCC mandates that the band must be split into at least 75 subchannels and that no subchannel is occupied for more than 400 milliseconds.
There is an ongoing debate about the security that this hopping feature provides. Though it is possible to monitor the hopping sequence and then wait till the whole sequence is repeated, the level of security is sufficient that expensive equipment would be required to break in.
Many FHSS LANs can be colocated if an orthogonal hopping sequence is used (see Orthogonal Frequency Division Multiplexing for more information).
Because the subchannels in FHSS are smaller than in DSSS, the number of colocated LANs can be greater with FHSS systems. The most commonly used standard based on FHSS is HomeRF.
- Orthogonal Frequency Division Multiplexing (OFDM). OFDM technique distributes the data to be transmitted into smaller pieces, which are simultaneously transmitted over multiple frequency channels that are spaced apart.
This spacing provides the orthogonality that prevents the demodulators from seeing frequencies other than their own.
When transmitting data using the OFDM, the data is first divided into frames and a mathematical algorithm known as Fast Fourier Transformation (FFT) is applied to the frame, then OFDM parameters (for example, timing) are added.
An Inverse Fast Fourier Transformation (IFFT) is then applied on each frame. The resulting frames are then transmitted over the designated frequencies. A receiver performs the inverse operations to get the transmitted data by performing FFT on the frames.
The benefits of OFDM are high spectral efficiency, resiliency to RF interference, and lower multipath distortion. In summary, wireless LAN adapters can use infrared, microwave, or radio frequency as transmission band.
Wireless LAN cards used in a given wireless network must use the same band. Wireless LAN adapters communicate with the physical media on the physical side of the reference model, and the MAC layer at the data−link layer.
Data−Link Layer
The MAC layer of the data−link layer (see Figure 6) controls how data is to be distributed over the physical medium.
The main job of the MAC protocol is to regulate the usage of the medium, and this is done through a channel access mechanism.
A channel access mechanism is a way to divide the available bandwidth resource between subchannels, the radio channel, by regulating the use of it.
It tells each subchannel when it can transmit and when it is expected to receive data. The channel access mechanism is the core of the MAC protocol.
With more companies and individuals requiring portable and mobile computing, the need for wireless local area networks continues to rise throughout the world.
Because of this growth, IEEE formed a working group to develop a media access control (MAC) and physical layer (PHY) standard for wireless connectivity for stationary, portable, and mobile computers within a local area.
As most wired LAN products use Carrier Sense Multiple Access with Collision Detection (CSMA/CD, also known as Ethernet) as the MAC protocol, it has been a logical choice for most wireless LAN equipment manufacturers and the standard bodies to incorporate the CSMA/CD or a similar protocol as the MAC protocol.
Most data−link layer implementations use either CSMA/CD or one of its derivatives, for example, Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA).
Carrier sense means that the station will listen before it transmits. If there is already someone transmitting, then the station waits and tries again later. If no one is transmitting, then the station goes ahead and sends what it has.
If two stations send at the same time, the transmissions will collide and the information will be lost. This is where collision detection comes into play. The station will listen to ensure that its transmission made it to the destination without collisions.
If a collision occurs, then the stations wait and try again later. The time the station waits is determined by using a backoff algorithm, which is essentially a structured mechanism for increasing the wait time.
This technique works great for wired LANs, but wireless topologies can create a problem for CSMA/CD. This problem is known as the hidden node problem. The hidden node problem is shown in Figure 7.
Node C cannot hear node A. So if node A is transmitting, node C will not know and may transmit as well. This will result in collisions. The solution to this problem is CSMA/CA. CSMA/CA works as follows: The station listens before it sends.
If someone is already transmitting, it waits for a random period and tries again. If no one is transmitting, then it sends a short message. This message is called the ready−to−send (RTS) message.
This message contains the destination address and the duration of the transmission. Other stations now know that they must wait that long before they can transmit. The destination then sends a short message, which is the clear−to−send (CTS) message.
This message tells the source that it can send without fear of collisions. Each packet is acknowledged, which means that upon receipt the receiver must send an acknowledgment (ACK) packet. If an ACK is not received, the MAC layer retransmits the data. This entire sequence is called the four−way handshake.
Access Points (APs)
An access point (AP) is a centralized wireless device that normally does not have any computer physically attached to it. The AP controls the traffic in the wireless medium. All traffic between the communicating computers must go through the access point.
Access points are often connected to the wired LANs (for example, corporate or home networks) that are usually connected to a wide area network (WAN)—for example, the Internet using a high−speed connection such as broadband (see Figure 8).
Access points are set up in this way, to route the traffic between the wireless LAN and the network that it connects with.
APs contain a wireless interface adapter just like any other computer in a wireless LAN.
In addition, APs maintain a lot more information about the computers in the network and perform the necessary authentication, encryption, and session (connection) management with all the connected computers.
If an AP is able to connect the wireless LAN with any other type of network, then it must also act as a router. In this case, it also contains a regular network interface card to participate in the other wired network.