In deployment scenarios where securing wireless LANs is crucial and the 802.11−standard wireless LAN security does not seem enough, alternate security measures can be adopted to provide a higher level of security.
These measures include authentication and privacy mechanism at network level by using supplementary technologies like 802.1X and virtual private networks (VPNs). In this section, we look at the ways in which the 802.1X authentication protocol and the VPN can be used to improve the security provided by the 802.11 standard.
The 802.1X Authentication Protocol
The 802.1X is an IEEE draft stand that defines a port−based network access control protocol (that is, one involving a network that uses more than one channel to perform network operations instead of using one channel for all operations).
802.1X was originally designed for Ethernet−based LANs, but it can also be applied to 802.11−based wireless networks. 802.11 does not require that all LAN devices use the same WEP keys, and allows a device to maintain two sets of shared keys: a per−station unicast session key and a multicast/global key.
Current 802.11 implementations primarily support shared multicast/global keys, but are expected to support per−station unicast session keys in the near future.
Managing and updating all of these keys can be a difficult manual process, and it does not scale appropriately in large infrastructure network or in an ad−hoc network.
In addition, the lack of an interaccess point protocol (IAPP), a protocol that will facilitate communication between two APs, further compounds key management issues when wireless LAN devices roam from one AP to another, since without this protocol, authentication has to begin anew.
The Basic 802.1X Operation
To understand the basic operation of 802.1X, let's define some of the entities involved in an 802.1X authentication protocol. These entities are authenticator, supplicant, and the authentication server.
An authenticator is an entity that enforces authentication before allowing access to services. The supplicant is an entity that requests access to services available via the authenticator.
An authentication server performs an authentication function: It checks the credentials of the supplicant on behalf of the authenticator. The authentication server then responds to the authenticator indicating whether or not the supplicant is authorized to access the authenticator's services.
The authentication server may be a separate entity, or its functions may be colocated with the authenticator. The most widely used authentication server is the Remote Authentication Dial−in User Service (RADIUS) server. Figure 1 shows a basic arrangement of 802.1X entities.
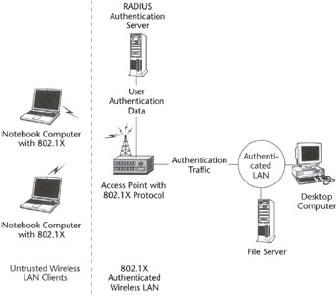 A LAN port can play one of two roles in a network access control interaction: authenticator or supplicant.
A LAN port can play one of two roles in a network access control interaction: authenticator or supplicant.
The authenticator's port−based access control defines two logical access points to the LAN via a single, physical LAN.
The first logical access point, labeled Uncontrolled Port, allows an uncontrolled exchange between the authenticator and other systems on the LAN—regardless of the system's authorization state.
The second logical access point, labeled Controlled Port, allows an exchange between a system on the LAN and the authenticator's services—only if the system is authorized.
One use of the uncontrolled port would be to provide a path for exchanges between the authenticator and the supplicant. The authorization state of the controlled port determines whether traffic can flow from the supplicant to the LAN through this port.
The authorization state will likely start as unauthorized, and then transition to the authorized state upon authentication of the supplicant. 802.1X typically uses Extensible Authentication Protocol (EAP) as a means to communicate the authentication information between the supplicant and authentication server.
This means that EAP messages need to be encapsulated directly over a LAN medium. Another protocol, EAP over LAN (EAPOL), was defined for this purpose.
An Example 802.1X
Exchange for Authentication In this example, we assume the use of EAP as the protocol for exchanging the authentication data, and a RADIUS server for an authentication server.
There are several other possible message flows depending on the authentication mechanism used. An example exchange that could take place to authenticate the supplicant might be as follows:
- The authenticator sends an EAP−Request/Identity message to the supplicant.
- The supplicant sends an EAP−Response/Identity with its identity to the authenticator. The authenticator forwards this to the authentication server.
- The authentication server responds with an EAP−Request packet containing a password challenge to the supplicant through the authenticator.
- The supplicant sends its response to the challenge to the authentication server through the authenticator.
- If the authorization is successful, the authorization server sends an EAP−Success response to the supplicant through the authenticator. The authenticator can use this success to set the controlled port state to authorize.
Using 802.1X to Solve the 802.11 WEP Security Issues
The basic 802.1X protocol must be extended to address security issues of 802.11. This is done by passing an authentication key to the client, and to the wireless access point, as part of the authentication procedure.
Only an authenticated client knows the authentication key, and the authentication key encrypts all packets sent by a client as defined in the WEP protocol.
802.1X helps the WEP problems by providing keys per station or per session to limit the number of packets using the same key, and by making sure that the keys are changed often—rekeying (changing the keys) as much as every 5 to 10 minutes or 4 million packets, therefore limiting the reuse of shared keys, the main weakness of the WEP protocol.
With 802.1X implemented and deployed, this can be accomplished automatically. Following authentication, the 802.1X protocol should be configured to request that the station reauthenticate periodically, at a specific time interval.
802.1X thus provides per−station, per−session keys, and causes these keys to be changed often, eliminating reuse issues. In addition, 802.1X allows for user identification and authentication and centralized authentication, authorization, and accounting support.
This also allows for the future use of extended authentication mechanisms. It is important to remember that all authentication traffic is communicated through the uncontrolled port, whereas all authorized data transfer takes place on the control port once the user has been authenticated.
Authentication of a wireless LAN adapter using 802.1X protocol consists of the following steps:
- Without a valid authentication key, an AP inhibits all traffic flow through it.
- When a wireless LAN adapter (supplicant) comes in range of a wireless AP authenticator, the wireless AP issues a challenge to the wireless station.
- Upon receiving the challenge from the AP, the wireless LAN adapter responds with its identity.
- The AP then forwards the wireless LAN adapter's identity on to the RADIUS server to initiate authentication services.
- The RADIUS server then requests the credentials for the station, specifying the type of credentials required to confirm the wireless LAN adapter's identity.
- The wireless LAN adapter sends its credentials to the RADIUS server.
- Upon validating the wireless LAN adapter's credentials, the RADIUS server transmits an authentication key to the AP. The authentication key is encrypted so that only the AP can access it.
- The AP uses the authentication key received from the RADIUS server to securely transmit—per−wireless LAN adapter unicast session and multicast/global authentication keys—to the station. This key is always transmitted in encrypted format.
Virtual Private Networks (VPNs)
Virtual private networks (VPNs) are typically used in TCP/IP−based networks to secure communication between remote users and a private network.
A typical usage scenario for a VPN can be a remote worker who uses a dialup connection from his or her home to connect to the Internet and uses VPN to establish a secure network session with the corporate network at the company he or she works at.
Using VPN to establish such connectivity guarantees that the remote user is authenticated and all data over the Internet is transmitted in encrypted form. The usage scenario we just discussed is shown in Figure 2.
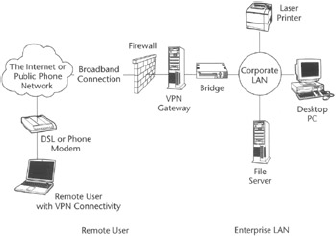 VPN technology can be used in the wireless LANs to provide user authentication and data privacy just like a remote user that accesses a corporate LAN over the Internet using VPN.
VPN technology can be used in the wireless LANs to provide user authentication and data privacy just like a remote user that accesses a corporate LAN over the Internet using VPN.
Some confusion may arise in deciding when to use a VPN and when to use 802.1X. These technologies actually complement each other, and there are times when both may be used.
VPN can be used in a variety of ways with 802.11−based wireless LANs to provide security between a user and the extended wired LAN, among users in a wireless LAN, and between a wireless user and an AP connected to a corporate LAN over the Internet.