The logical architecture of a network refers to the structure of standards and protocols that enable connections to be established between physical devices, or nodes, and which control the routing and flow of data between these nodes.
Since logical connections operate over physical links, the logical and physical architectures rely on each other, but the two also have a high degree of independence, as the physical configuration of a network can be changed without changing its logical architecture, and the same physical network can in many cases support different sets of standards and protocols.
The OSI Network Model
The Open Systems Interconnect (OSI) model was developed by the International Standards Organisation (ISO) to provide a guideline for the development of standards for interconnecting computing devices.
The OSI model is a framework for developing these standards rather than a standard itself — the task of networking is too complex to be handled by a single standard. The OSI model breaks down device to device connection, or more correctly application to application connection, into seven so-called “layers” of logically related tasks.
- Physical layer - Standards to control transmission of the data stream over a particular medium, at the level of coding and modulation methods, voltages, signal durations and frequencies.
- Data link layer - Standards to specify the way in which devices access and share the transmission medium (known as Media Access Control or MAC) and to ensure reliability of the physical connection (known as Logical Link Control or LLC).
- Network layer - Standards to define the management of network connections — routing, relaying and terminating connections between nodes in the network.
- Transport layer - Standards to ensure reliable completion of data transfers, covering error recovery, data flow control, etc. Makes sure all data packets have arrived.
- Session layer - Standards to manage the communication between the presentation layers of the sending and receiving computers. This communication is achieved by establishing, managing and terminating “sessions”.
- Presentation layer - Standards to control the translation of incoming and outgoing data from one presentation format to another.
- Application layer - Standards to define the provision of services to applications — such as checking resource availability, authenticating users, etc.
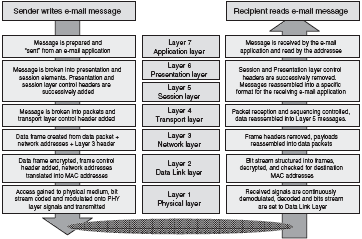
An example will show how these layers combine to achieve a task such as sending and receiving an e-mail between two computers on separate local area networks (LANs) that are connected via the Internet. The process starts with the sender typing a message into a PC e-mail application (Figure 1).
When the user selects “Send”, the operating system combines the message with a set of Application layer (Layer 7) instructions that will eventually be read and actioned by the corresponding operating system and application on the receiving computer.
The message plus Layer 7 instructions is then passed to the part of sender’s operating system that deals with Layer 6 presentation tasks. These include the translation of data between application layer formats as well as some types of security such as Secure Socket Layer (SSL) encryption.
This process continues down through the successive software layers, with the message gathering additional instructions or control elements at each level. By Layer 3 — the Network layer — the message will be broken down into a sequence of data packets, each carrying a source and destination IP address.
At the Data Link layer the IP address is “resolved” to determine the physical address of the first device that the sending computer needs to transmit frames to — the so-called MAC or media access control address.
In this example, this device may be a network switch that the sending computer is connected to or the default gateway to the Internet from the sending computer’s LAN.
At the physical layer, also called the PHY layer, the data packets are encoded and modulated onto the carrier medium — a twisted wire pair in the case of a wired network, or electromagnetic radiation in the case of a wireless network — and transmitted to the device with the MAC address resolved at Layer 2.
Transmission of the message across the Internet is achieved through a number of device-to-device hops involving the PHY and Data Link layers of each routing or relaying device in the chain.
At each step, the Data Link layer of the receiving device determines the MAC address of the next immediate destination, and the PHY layer transmits the packet to the device with that MAC address.
On arrival at the receiving computer, the PHY layer will demodulate and decode the voltages and frequencies detected from the transmission medium, and pass the received data stream up to the Data Link layer. Here the MAC and LLC elements, such as a message integrity check, will be extracted from the data stream and executed, and the message plus instructions passed up the protocol stack.
At Layer 4, a protocol such as Transport Control Protocol (TCP), will ensure that all data frames making up the message have been received and will provide error recovery if any frames have gone missing. Finally the e-mail application will receive the decoded ASCII characters that make up the original transmitted message.
Standards for many layers of the OSI model have been produced by various organisations such as the Institute of Electrical and Electronics Engineers (IEEE). Each standard details the services that are provided within the relevant layer and the protocols or rules that must be followed to enable devices or other layers to call on those services.
In fact, multiple standards are often developed for each layer, and they either compete until one emerges as the industry “standard” or else they peacefully coexist in niche areas. The logical architecture of a wireless network is determined principally by standards that cover the Data Link (LLC plus MAC) and PHY layers of the OSI model.
The next tutorial starts this introductory sketch one layer higher — at the Network layer — not because this layer is specific to wireless networking, but because of the fundamental importance of its addressing and routing functions and of the underlying Internet Protocol (IP).