Network operational security ensures that a given network is equipped with best−known and appropriate measures to guarantee a reliable, safe (ensures that precious data within the network is never compromised), and intrusion−free (free from the possibility of unauthorized access by intruders or hackers) network.
It makes sure that the network is well guarded against malicious attacks and intentions to intrude on the privacy and safety of the network, both from adversaries who are not authorized to access the network and from those who are authorized users of the computer network.
To allow a trouble−free operation, operational security includes proactive measures for setting up policies that define how physical access to networking devices will be restricted.
It defines and restricts access to the network based on identity (does not allow network access to an individual without proof of their identity) using network access control or authentication, and controls how the network is connected to the Internet or to another network.
The purpose of network security is to prevent and detect unauthorized use of computing and network resources. Prevention measures need to be developed so that unauthorized users can be prevented from accessing part of the computer network they are not allowed to.
Detection is necessary in determining attempted and successful network breaches and identifying the systems and the data that have been compromised.
Network security is necessary not only to protect the data from unauthorized access but also to protect an unauthorized user from initiating fraudulent transactions under false pretenses such as forged emails or financial transactions.
To adequately secure a network, we need to have a comprehensive plan. In formulating such a plan, we need to consider physical security as well as network authentication and access control; user rights; and user access to workstations, servers, disk space, and printers.
In here, we'll talk about the security issues relating to LAN resources that affect both local and remote LAN users. We talk about physical security, network authentication and access control, common attacks on networks, and ways to ensure operational security in a wired LAN environment.
Physical Security
Physical network security deals with securing physical computing assets and resources from the adversaries. Most common physical security issues include theft and network hacking through penetrating into the physical network cable.
To protect wired networks from theft, in most cases, a well−controlled premises entry system with safeguards against intrusion is necessary. This normally includes a safe environment where computers and networks are located in a hazard−free environment.
This hazard−free and safe environment must be premises onto which only authorized personnel are admitted. Network cabling needs to be secured through impenetrable conduits. All connections and network jacks need to be monitored regularly and unused jacks disabled.
Servers, routers, and network communication equipment should be located in areas only accessible by authorized personnel. A well−documented chain of custody must be maintained for servers with sensitive data.
Central networking resources, such as servers, routers, and network communication resources, should be supplied with conditioned and redundant power systems such as using surge protectors and uninterruptible power supply (UPS) to protect against power−related problems such as surges, blackouts, and brownouts that can cause physical damage and harm electrical components.
Data should also be backed up on a regular basis, and offsite data storage must be maintained. Comprehensive disaster recovery plans should be developed, and regular disaster recovery drills must be conducted.
Network Authentication and Access Control
In most cases, the first entry point to a network is through a user workstation. The mechanism of ensuring that a rightful user is accessing the network by validating the authenticity of a user is commonly known as authentication or login.
Login is a process that identifies the authenticity of a user based on the credentials he or she provides (for example, username and password). Upon successful login, the user is granted access to the network resources (for example, file servers and printers).
Preventing unauthorized access to a network is of primary importance when discussing LAN security. In most LANs, the user workstations are installed with operating systems (OS) with various levels of built−in authentication features.
Most computers allow multiple users to log in and use the system resources. Depending on the OS, the user may log in locally (physically connected to the network), or remotely (for example, connected over the Internet) by authenticating over the network.
In either case, the user who wants to access the workstation must be preauthorized to log in. The users are authenticated via a central server called a login server.
Each user authorized to access a network must have an account on this login server. The network administrator usually creates these accounts. The privileges and authorization levels are granted to each user when a user account is created.
In LAN terms, a given "privilege" normally relates to the type of access a user has over network administration (for example, user account management), whereas authorization refers to a set of permissions that a user is granted to use network services (for example, authorization to access an internal human resources database).
Privileged logins, commonly referred to as root or administrator users, should be limited to a small number of authorized users. Access to resources should be mapped through groups of users aggregated in logical collections.
For example, in an enterprise setting, users from accounting should belong to a group consisting only of employees working in the accounting department and resources like accounting servers should be restricted to that group.
User authentication information is stored in many different ways, which varies in each operating system. However, the standard that is gaining popularity in both the UNIX and Windows 2000 environments is known as lightweight directory access protocol (LDAP).
LDAP is a TCP/IP−based protocol used to access user information stored in a specialized database known as an LDAP directory. This directory contains the information necessary to validate the authenticity of a network user. LDAP is supported on Windows 2000, but Windows XP is based on LDAP.
Lets talk about individual network user authentication, user groups, authentication servers and access control lists (ACLs), and remote user authentication.
Network User Authentication
The most commonly used mechanism for validating the identity of a user from a known authoritative source is called authentication. Network user authentication is used to ensure that only those personnel who are duly authorized can access network resources.
Typically, to be authenticated, the user is presented with a screen that collects multiple pieces of information, some of which are well known to all users of the system (for example, a username or login) and some of which are known only to that particular user (for example, a password or a secret word).
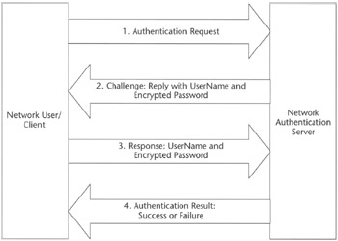
Generally, a username (login name or screen name) would be known to all participating in a network, and a password that is only known by that user is also required in such a screen. Figure 1 shows a network authentication dialog that requires a user to enter username and password.
This is known as single factor authentication because it has only one component (password) private to the user.
Normally the authentication information is communicated from the user workstation to the server in a secure manner.
For example, Microsoft Windows 2000 uses a challenge−response mechanism in which the server first issues a challenge to the user.
For example, asking for information such as username and password—and the user has to provide the correct response to the challenge.
In most systems, the passwords are kept on the server in an encrypted format. Figure 1 shows a generic network authentication process.
The client computers typically collect the password in human readable form known as cleartext and present it to the server in an encrypted form.
Whenever the user requests authentication, the server matches the encrypted password with the one stored in the password database. Depending on the security needs and the operating system, there may be several levels of passwords that are requested by the server before a user is allowed to access a resource.
Although the username and password combination remains the most widely used method of authentication, other means of authentication such as biometric (for example, retina scan or fingerprint) or hardware−based strong cryptographic tokens (for example, smart cards) are being used in scenarios where a higher level of network security is desired.
The authentication mechanisms that require more information than just username and password are called n−factor authentication, where n is the number of additional pieces of information that is required to log in. For example, if besides the username and password a retinal scan were also required, it is called a two−factor authentication.
User Groups
In most network deployment scenarios the number of network users directly depends upon the number of personnel in an organization; they do not normally all perform the same job task, nor does everyone manage the network operation.
For example, a computer network in an accounting firm with 100 employees may have 60 accountants, 20 administrative support personnel, 10 executives, 5 facility coordinators, and a 5−person information technology (IT) department.
Each set of users may need a different set of services—for example, accountants may need access to accounting software and email, executives to confidential data, and IT to the entire network to be able to manage it.
To manage and secure access to a given set of services to a set of users is a common construct in security schemes known as user groups. Generally, a user group consists of a collection of one or more users with a unique identifier or name known as a group name.
Often users are grouped on the basis of their job function or role within the network environment, and they are assigned appropriate permission to access various network resources.
For example, all the users in accounting might belong to a group called accounting, likewise a group to which all users in the facility department belong may be called facilities, and computer systems administrators may belong to a group called sysadmin with permission to access all systems except the servers that contain confidential trade secrets and those containing human resource information.
In some systems, user groups can contain other groups, resulting in a hierarchy—for example, accountants who deal with clients in Europe may belong to a group known as eu−accountants as a subgroup of accountants.
In essence, user groups provide a higher level of network security and improved network performance by allowing access to the protected network resources only to users in selected groups.
Authentication Servers and Access Control Lists (ACLs)
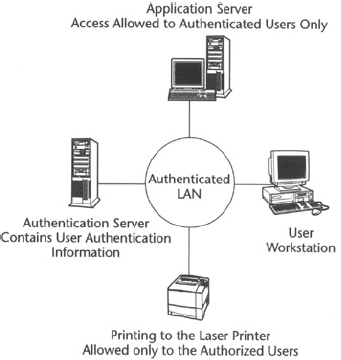
Authentication servers are the computers that perform the authentication of all network users who wish to access the network. The authentication servers maintain the list of users, groups, and passwords, and the privileges they have. Figure 2 shows an authentication server in an authenticated network.
This list is known as an access control list (ACL). Access control lists are kept safe and are only managed by a small number of users who are normally the network administrators.
Besides having an authentication server, each computer on a network may have its own authentication mechanism and ACLs if it wishes to allow other network users to access its resource.
For example, a networked computer equipped with a high−performance printer may require authentication from those who want to print so as to reduce the cost that the high−performance printer incurs.
Likewise, in the Microsoft Windows operating system, file−sharing is controlled using authentication servers and access control lists to restrict access to authorized users only.
Remote User Authentication
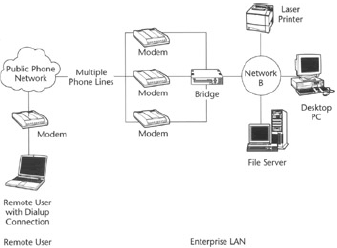
If network users are not present onsite where the physical computer network exists and these users are provided access to the network from remote sites (for example, client site, or from home), then extra security measures are needed to allow users to remotely and securely log on to a network.
Onsite users are said to be operating in a trusted environment because they are directly connected to the network. Figure 3 shows a remote user connected to a LAN using a dialup connection.
Remote users typically access the network through unsecured channels (for example, phone lines or the Internet) and present higher security risks to the overall network.
Typically, remote users are authenticated using an extra level of security in addition to the username− and password−based authentication.
Most remote network users are authenticated using standard network protocols; we talk about some of these protocols later.