The main thing to remember about hotspot security is that you probably won’t use the encryption features or password authentication for users with your access point or any other fancy security features unless your hotspot is located in Japan (where encryption is required).
Most hotspots use “Open Authentication” (no encryption) instead of WEP, which is called a “Preshared Key Authentication” method. Keep in mind that WEP only authenticates a device, and it is assumed that if users know the key that they are allowed to connect.
Other encryption methods, such as TKIP or AES, allow only Open Authentication. In all cases your hotspot will not be authenticating a user as is done on the network with a challenge/response mechanism (username and password).
The counter argument for enabling encryption is that it makes communication more secure and less easily sniffed by other computers. The extra difficulty connecting users with encryption and the reduction in throughput has to be weighed against the probability that someone may try and compromise your guest’s communications.
We feel that sensitive information sent to a non-secured site is something that is a problem in and of itself, and encryption won’t help that. So we tend to opt for ease of use and count on users to implement their own security features.
However, many other knowledgeable experts would disagree on this point. Don’t pay more to get a device that implements unusual security measures because you are going to leave them off so that the public can more easily connect.
However, you should make sure that each of your users has a firewall set on their computer. If they don’t have software such as Norton Personal Firewall, Zone Alarm Pro 4, or Black Ice (for Windows, for example), then at least remind your users to set the firewall that their operating system offers them.
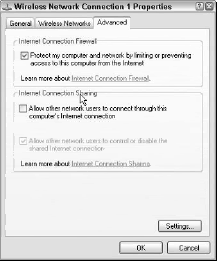
That firewall is turned on in the Advanced tab of the Network Connection properties sheet of a Windows XP connection, and is a checkbox called the Internet Connection Firewall that says “Protect my computer and network by limiting or preventing access to this computer from the Internet”.
In Windows XP Service Pack 2 the new Security Center will provide just such a reminder. Although the current 802.11 protocols are not easy to make secure, we hope the release of 802.11i will offer some help. Until then there are some things you can do to help make your hotspot more secure:
- Make sure your network doesn’t extend beyond your physical location.
- Don’t broadcast your WLAN’s router’s network ID (SSID).
- Remind customers that unencrypted transfers can be read and that sensitive information such as personal information, credit card numbers, and passwords should be avoided on non-secure connections. Stealing information over a WLAN is not uncommon.
- Don’t leave your router/access point’s IP address, login name, or password set at the default. If your AP offers the username “admin” with no password, for example, change both of them.
A bad guy only needs to look up your AP’s manual online to know what the defaults are. Sometimes a router such as the Apple AirPort maintains an address that can’t be changed.
- Use a strong firewall and put your wireless network on its own subnet.
- Do not allow your clients’ computers to connect under a peer-to-peer network connection; that is, disable the “ad hoc” mode and enable the infrastructure mode on your router or AP.
- Make sure that connected computers are password-protected, both at a system and a shared file/folder level.
- Know your users. Make sure you have approved the people on your WLAN and that you monitor their activity to make sure that there are no rogue users. If you are registering users, you can enable the known MAC address feature of your AP and only permit known users to connect; something you can’t do if your WLAN is meant for general public access without authentication.
- Turn off all wireless devices not in use, and that means every night if necessary. Test on a regular basis that when all of your wireless devices are turned off there is indeed no wireless signal that can be detected. Unauthorized access points are a security threat.
- Block TCP ports 135, 137, 138, 139, and 445 to directory, file, and printer sharing information to be transmitted. Disable NetBIOS over TCP/IP as well. You can do this in your firewall’s software, in security software, and as part of your proxy server or router.
If your business network is going to use the hotspot connection, make sure you have a robust firewall or gateway between your LAN and your access point or router.
Frankly, given that access points and routers are as cheap as they are these days you are better off buying additional wireless devices and keeping your network’s wireless connection separate—why take additional risk?
Any wireless connection on your business network needs to be encrypted and secured.