When you configure your WLAN adapters via the Windows XP dialog boxes, with the Wireless Networks tab set to allow Windows to perform wireless configuration automatically, as soon as you choose either of the WPA settings, WPA or WPA-PSK, Windows enables IEEE 802.1x authentication for your adapter as well.
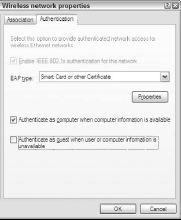 Figure 1 shows the setting in place, as indicated by the grayed-out checkbox instructing Windows to enable this technology.
Figure 1 shows the setting in place, as indicated by the grayed-out checkbox instructing Windows to enable this technology.
IEEE 802.11x authentication goes hand in hand with wireless networks, particularly those configured to use WPA or its eventual successor, 802.11i.
In Windows XP Service Pack 1 and later, as well as in the Windows 2003 Server operating system, you can enable 802.1x authentication only on infrastructure networks that require a network key for access.
In other words, you can use 802.1x authentication for WEP as well as WPA-encrypted networks, and Microsoft encourages you to enable it for both, but when you put WPA in place, Windows does the job for you.
To use this authentication method, Windows needs to know the Extensible Authentication Protocol (EAP) type you wish to use. The default, and the one you should stick with until you know your AP or server can handle anything else, is Smart Card or Other Certificate.
As mentioned, there’s no need to change this; as long as your network connects successfully, the authentication is in place (it’s part of Microsoft’s attempt to automate all wireless configurations).
However, you have several choices besides this default, both an entirely different EAP type and numerous options accessed via the Properties button with the Smart Card option selected.
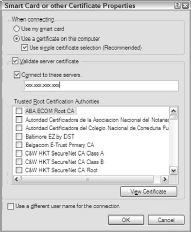 Figure 2 displays the result of clicking that Properties button.
Figure 2 displays the result of clicking that Properties button.
Here you can see numerous possible locations from which your WLAN adapter can acquire the certificate information necessary to continue.
If you have a specific server that stores certificates you can use (as on a larger business network), check Connect to these Servers and fill in the server details (as supplied by your network administrator).
The list of Trusted Root Certification Authorities in the large pane in the middle of the dialog box provides numerous certificate types that you can instruct Windows to use, but again you would find these in place in a business or organizational network, never a home or even small office network.
If you know the certificate you are to request, check the appropriate box; otherwise, leave the defaults in place. The Validate Server Certificate checkbox lets you instruct your PC to guarantee that the certificate used for these purposes remains valid, by checking its credentials.
Returning to the Authentication tab, you can click the EAP Type drop-down menu and select the alternative EAP type, PEAP. Protected EAP (PEAP) extends the EAP protocol to enable highly secure transactions in a manner similar to a virtual private network, by creating a secure tunnel in which the packets can move.
Specifically, EAP provides a flexible alternative to EAP-TLS (Transport Layer Security), improving on EAP-TLS itself by removing the requirements to install and manage certificates on the clients.
Essentially, PEAP begins by authenticating the connection, by using digital certificate technology, and then creates the encrypted tunnel along with encryption keys for the data. The data is not only encrypted, but also checked for integrity, as it moves through the connections.
Again, on a home or small office network you will have little reason to consider PEAP. But its prominence on the Wireless Network Properties dialog box points to the increased concern by Microsoft and, as should now be apparent, by all wireless networking vendors and technologists, for WLAN transmission security.
You will see services in the near future to provide increased security for even small WLANs, through a certificate lease or rental kind of configuration, just as security services for standard LANs are now available from third parties.
This is all good news, of course, for anyone with even a small home network, because while you could argue that the data you transfer over your personal WLAN is of less overall importance the data that travels through a corporate WLAN, in fact this assumption is only partly valid.
True, your personal data affects fewer people, but you have far fewer means of recovering from data or resource theft, and you don’t have anything approaching limited liability in matters surrounding your own life.
The point is, of course, that securing your WLAN should become a top priority for you, no matter how insignificant it may seem, and WPA, with its extremely friendly WPA-PSK subset, lets you do precisely that.