One of the basic uses of computer networks is to share data among its users. The information contained in data is often confidential or private. In business environments it could be trade or business secrets, a hidden policy, or classified information.
At home, it could be personal emails, pictures, or contracts. All such data must be protected from anyone who should not have access to or knowledge of such information. In a networked environment, such data is vulnerable to be shared or tampered with without your knowledge.
For example, let's imagine that Alison, our imaginary naive computer user, had a very personal file that she did not want anyone to see and she saved it on her computer at work.
Since the directory in which she left the file was shared on the Internet, the file was hacked and the very next day she was the talk of the town. Not only are the files residing on a networked computer at risk, but also the data that leaves your computer can be sniffed (seen) by network−monitoring software that has access to the network.
One example might be that you sent an email over the Internet to a friend of yours about a multimillion dollar deal that you are engaged in, given that by default all Internet email goes through a number of computers in cleartext (human readable text format).
A hacker got hold of the details of the deal, and he or she turned all your dreams into a nightmare by publishing the information on the Internet. This problem is further complicated when remote users connect to a LAN through the Internet.
In this scenario, if the data between the remote computer and a user inside the LAN is exchanged in cleartext, all the data transmitted is vulnerable to examination and tampering if it is sniffed by a hacker.
The primary concerns in electronic and network data security are confidentiality and integrity. Where confidentiality means that information can only be accessible by the intended recipients, and integrity means that data cannot be tampered with.
Data in a network is vulnerable to both confidentiality and integrity attacks both while it is residing on a computer as well as while in transit between computers on a network or among networks (for example, over the Internet).
Let's talk about how data is vulnerable to attacks while residing on a computer. We look at the ways the data is secured and briefly discuss the basic cryptographic primitives and how they are generally used to protect and secure network data.
Resident−Data or File Security
Sensitive data residing on a computer's hard disk or on a file server is vulnerable to both confidentiality and data integrity attacks. An adversary can look at the data, gaining information that he or she should not have, or alter the data so that it does not carry the exact meaning it should.
An example of such vulnerability would be a file containing secret contract information residing on a network file server that is read by an authorized or unauthorized user.
Notice that the file system and network operational security alone cannot meet this vulnerability issue as a user, though authorized to access a particular folder, should not have the ability to read the file.
Protecting Data Using Cryptographic Primitives
The Merriam−Webster Collegiate Dictionary (online version available at www.m−w.com) defines the word cryptography as "the enciphering and deciphering of messages in secret code or cipher."
Cryptography is the mathematical discipline that is used for keeping information secret and guaranteeing integrity. The most basic cryptographic primitives include encryption (encipherment) and decryption (decipherment).
Cryptography has been used for centuries for protecting data confidentiality and integrity. A classic example for the cryptographic procedure is Caesar cipher, known to have been used by the Roman emperor himself for sending messages to his army.
In modern days, cryptography is used to protect electronic data from attacks that can damage its confidentiality and integrity. Let's look at the fundamentals of encryption and decryption mechanisms and talk about some basic techniques that use cryptographic mechanisms to ensure network data security.
Data Encryption and Decryption
Data encryption is the technique by which known data (that is, plaintext) is transformed into garbled data by using a cryptographic primitive commonly known as a cipher. Substitution ciphers are the simplest ciphers.
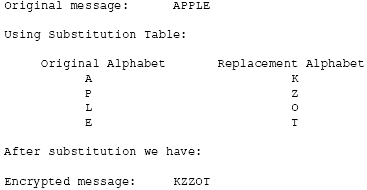
In substitution ciphers, each letter of the alphabet is substituted by another letter. For example, let's assume that our original message was APPLE; we substitute all occurrences of letter A with letter K, P with Z, L with O, and E with T, then our substitution cipher would work as shown in Figure1.
Caesar cipher is one of the oldest substitution cipher techniques ever used. In Caesar cipher, the text to be secured is encrypted by replacing each letter of the message with the third letter to its right.
For example, A is replaced with D, E replaces B, and Z is replaced with C. Decryption is the process that enables one to recover the original message from a message that was previously encrypted.
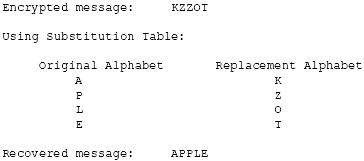
To recover the original message APPLE in our example, we need the encrypted message KZZOT and the table that was used to encrypt the message. The decryption in substitution ciphers is the reverse of the encryption process.
Let's recover the original message by substituting K with A, the two Zs with two Ps, O with L, and T with E. The recovered message is shown in Figure 2.
The procedure used to perform the cryptographic operation is called an algorithm, the original message is called plaintext, and the encrypted message is called ciphertext.
The table or characters used to encrypt a cryptographic message is known as the encryption key; likewise, the key that is used to decrypt a cryptographic message is called a decryption key.
In our substitution ciphers, both the decryption and the encryption keys were the table used to substitute the letters in the original message. Though substitution ciphers are still used for simple message encryption where security is not a concern, most currently used cryptographic algorithms are far more complex than substitution ciphers.
There are two types of encryption algorithms: symmetric encryption algorithms and asymmetric algorithms. Symmetric algorithms utilize the same key for both encryption and decryption, whereas asymmetric algorithms employ different keys for encryption and decryption.
Examples of symmetric algorithms include Advanced Encryption Standard (AES), Ron's Code 4 (RC4), Data Encrpyption Standard (DES), and Ron's Code 5 (RC5). The most widely used asymmetric algorithms include Rivest, Shamir, Adleman's RSA algorithm, and Whitfield Diffie and Martie Hellman's Diffie−Hellman algorithm.