The security tips presented so far in "WLAN Security Quick Tips" are relatively simple steps you can take to secure your network without digging too deeply into your AP’s management interface. If you’re willing to work a little harder at configuring your AP, however, we outlines some advanced techniques you might want to implement.
You could certainly argue that there’s no such thing as too much security. You’ll need to decide for yourself, though, if the time investment to implement these tips is worth it to you.
Upgrade Your Firmware
Access point manufacturers continually enhance their products by releasing new versions of the firmware, the software built directly into the device that enables the device to function with all its features.
Firmware updates typically fix bugs in the existing software, but they also can add features and improve performance in specific areas. Often after a firmware update, you’ll notice additional configuration items or even entire configuration screens, but usually the changes are relatively minor.
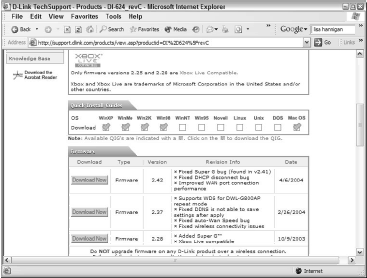
In some cases, you can even lose features, as shown in Figure 1.
Here, the D-Link DI-624 firmware page states that only versions 2.25 and 2.28 are compatible with the Xbox Live gaming system; downloading and installing the latest version on this page, 2.42, would render the game console inoperable for live play.
The importance of upgrading firmware lies primarily in the enhancement and repair of security features. Frequently, no such enhancements exist, mostly because the manufacturers focus considerable attention on getting those features correct from the beginning, even at the expense of other less important items.
Visit the firmware upgrade page regularly, however, to determine if a security fix has become available, and if so, download and install it immediately, even if you do lose the ability to play Halo online.
Don’t Allow Remote Management
The ability to manage a network remotely provides the convenience of not having to physically move to a PC experiencing problems. Unfortunately, the legitimate administrators aren’t the only ones who find remote management convenient; so do all the intruders out there looking for a way to break into unsecured networks.
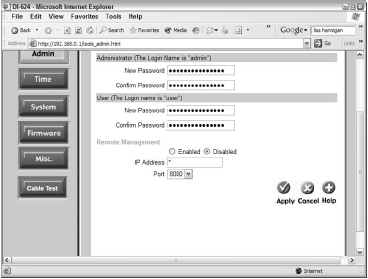
An intruder need only fire up a Web browser, type in the IP address of the router or AP, and open the configuration utility after that. Figure 2 shows the small but important Remote Management configuration items for the D-Link DI-624.
By default, D-Link disables this feature, but some manufacturers set the default to Enabled, especially on older routers. Note the asterisk in the IP Address field.
If you enable the feature with this setting in place, any computer on the Internet can remotely manage the router/AP as long as the user knows the IP address and the admin password. Not good.
If you absolutely need remote management in place, be sure to change the password to the configuration utility frequently. In addition, if you’re logging in from a PC with a fixed IP address, specify that address as the only legitimate address for remote management.
But unless you absolutely need this capability, simply leave it disabled for maximum security.
Use Static IP Addresses
DHCP brings something approaching magic to your network. Instead of opening the configuration dialog boxes of each network PC, you set them to acquire network addresses (IP numbers) automatically, and the DHCP server takes care of the rest.
In the case of an infrastructure WLAN working in conjunction with a cable/DSL router and a broadband modem, you actually have three DHCP servers in place: your router, your access point, and your Internet service provider’s server.
The broadband router acquires an IP from the Internet service provider’s DHCP server, and in turn acts as a DHCP server for the AP. Once the AP has acquired its IP from the router, it then turns around and provides DHCP service for the WLAN adapters. At each stage along the line, anyone accessing the DHCP server can also access the network.
This isn’t much of a problem in the case of either the broadband modem or the cable/DSL router, because both require that the would-be user connect the PC via Ethernet cable, an obvious physical difficulty if the user isn’t actually in the building or the switch room.
Anyone who knows the SSID name of your wireless LAN, however, can gain access without any physical connection because the AP happily provides an IP address to that user’s machine via its DHCP technology.
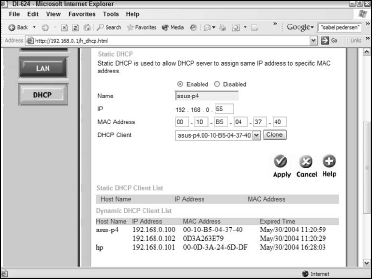
To get around this vulnerability, stop your AP from assigning IP numbers dynamically (automatically). All of today’s APs offer this option, typically available from the DHCP settings screen. Figure 3 shows the configuration screen for the D-Link DI-624 that allows this to occur.
Static IPs work by tying each IP address to the MAC address of the network adapter. An abbreviation for Media Access Control address, the MAC address is also known as the physical address, and refers to the unique identifier of each adapter—or, practically speaking, each PC.
Your DHCP configuration screen reports the MAC address of each adapter it has located. But you can determine the MAC address yourself by opening a Command box in Windows XP or 2000 and typing ipconfig /all.
The extensive amount of information presented as a result of this command includes a variety of addressing information, with the MAC address at the bottom, labeled as Physical Address.
In the D-Link screen shown in Figure 3, the AP labels the DHCP Client with a combination of the host name (the name you initially gave the computer) plus the MAC address.
The MAC address is significant in the configuration of static DHCP. To assign a specific address to a specific PC, you need to enter the MAC Address of that PC into the appropriate fields on the configuration screen.
In effect, you conjoin the IP address with the MAC address, whereas in a dynamic IP situation the DHCP server performs the joining at the time of connection, assigning whatever IP address comes next to that particular MAC address.
When configured for static IP, the AP reserves each IP number for a particular MAC address, allowing no other adapter but that one to acquire that IP address. Even after typing the MAC addresses and assigning them an IP number, you’re still not finished.
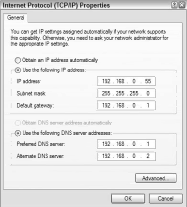
You now have to sit at each network PC, open the TCP/IP configuration dialog boxes, and type the specific IP number assigned to that PC.
Figure 4 shows the Internet Protocol Properties dialog box for the same PC as that was assigned in Figure 3, this time with the IP address, subnet mask, and DNS servers entered manually.
In the typical dynamic DHCP setup, these fields would remain empty, and the DHCP server would provide them to the PC.