It’s never enough. You get your ad hoc wireless network up and running, and you think you’ve got it made. Then you get an infrastructure network up and running, and you think you’ve got it really made.
But then you start reading about all the ways in which intruders can access your WLAN, and suddenly things don’t look quite so rosy. Despite everything you’ve accomplished—and believe me, getting a wireless network going is nothing to sneeze at—you realize your network contains several vulnerabilities.
Among other things, you realize you can see straight into the Shared Documents folder of not only the PCs on your own LAN, but those of the people who live next door as well.
So you start thinking that if you can see them, they can probably see you, and that’s simply not what you want your neighbors to be able to do. Add to this the newfound stress over those people who drive around locating open wireless networks, and you start considering the possibility of shutting your WLAN down completely.
Well, don’t. Although wireless networks offer more than their share of security concerns, you have a wide range of options at your disposal which, either individually or in conjunction with one or more other options, can render your WLAN increasingly difficult to crack.
It takes very little time to improve your WLAN’s security even a small amount. You don’t have to know anything about WEP, WPA, or anything else of even that technical a nature.
Just change a few of the default settings for the WLAN equipment, toss in a few Windows tricks and a few more simple everyday tips for all types of computers, and you’ve filled in the most obviously open holes.
Change Your Admin Password
Your first step in security anything on computers is to change the default password that lets you into the administrative utility. Whether you’re working with an access point or a router/AP combination, the admin utility has a default password that you can change within that utility.
Locate it and make the change so that an intruder into a networked PC can’t access the utility. As with all other passwords, make it difficult to figure out, writing it down for your own access if it’s too difficult for you to remember yourself.
Stop Broadcasting Your SSID
When you broadcast your SSID, you make it easier for legitimate users of your WLAN to connect to your network because the WLAN adapters can “see” the access point and connect automatically.
Unfortunately, you also make it easier for everyone else in the area to connect as well because broadcasting an SSID is very much like broadcasting a radio show: it’s available to anyone who tunes to that frequency.
Of course, radio stations want as many listeners as possible, and the last thing they try to do is keep people away. If you want a wide-open neighborhood network, by all means operate the same way.
But most of the time, of course, you don’t. You want your WLAN available only to a restricted group of users, and for that reason you should stop the open broadcast.
Interestingly, access point vendors tend not to see the SSID broadcast issue as particularly significant. APs typically default to having SSID broadcast enabled as part of the factory setup, and in some cases, disabling this feature takes some digging.
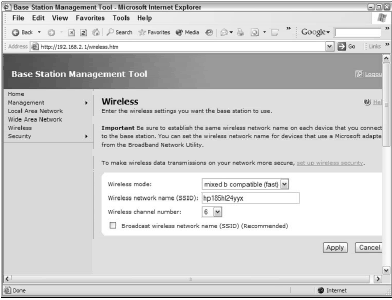
In the case of the Microsoft Wireless Base Station, the option to disable SSID broadcasts conveniently resides on the main page of the Wireless configuration screens (see Figure 1), available simply by clicking Wireless from the main menu on the left, although strangely enough WLAN security configurations occupy another screen entirely.
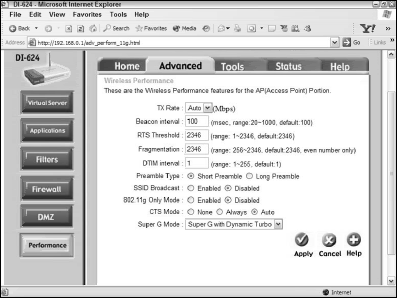
By comparison, with the D-Link DI-624 you need to drill down to the Performance screen on the Advanced tab. Figure 2 shows this screen, with the option for SSID Broadcast disabled.
What’s the effect of disabling the SSID broadcast?
Simply this: You need to know the SSID of the network before you can connect to it. The principle is similar to the classic interface design principle that recognition is easier than recall.
Menus and icons work better than command lines for many users because on the former you simply see the choices and select from among them, while command lines force you to remember what you need to type, and if you’ve never used a particular command before, you won’t be able to use it now either.
A broadcast SSID is analogous to the menu/icon interface, with the user presented with the name of the SSID, while refusing to broadcast SSIDs forces the network user to manually type it into the configuration dialog boxes for each client PC.
If the user doesn’t know it, the PC cannot connect. As you might suspect, even this doesn’t do the trick, unless you change something else: the SSID itself. Which brings us to the next tip.
Change Your SSID
If you’ve already stopped broadcasting your SSID, you might very well ask why it matters if you change it. Because, quite simply, most SSIDs are known whether or not they’re broadcast.
Access points ship with factory settings in place, and one of these factory settings is the default name of the SSID. Typical defaults include “wireless” and, in fact, “default” itself, and anyone with even a small degree of background in setting up APs, let alone trying to steal their signals, knows these defaults very well.
All would-be intruders need do is configure their WLAN adapters with a default SSID, and chances are they’ll find an AP for the connection. As a result, you should never, ever operate a wireless network with a default SSID.
After configuring your AP not to broadcast its SSID, open the configuration screens again and change the SSID to something an intruder will find hard to guess. As with a password, use a combination of letters, symbols, and characters, to further throw intruders off the scent.
Take a pet’s name, for example, and add some characters to it, so your dog Ralph becomes ra5lp3h. Make it so you can remember it, but no one else will guess. The SSID ra5lp3h might mean: Ralph is 5 years old and he’s my third dog. Who’d know?
In a business setting, of course, you might want something less personally based, but the idea is the same. Not only should you change your SSID as soon as you start using your AP, you should change it periodically as well.
Create a set of ten SSID names and rotate them, or just keep coming up with new ones. Yes, you have to reconfigure all the WLAN adapters in your network’s clients, but that’s far better than having your WLAN compromised.
Unplug Your Access Point
Okay, maybe this tip comes close to offending because of its sheer simplicity, but it’s absolutely valid: when nobody needs to use your WLAN, turn it off by unplugging it (most router/Access Point devices don’t have power switches).
For a home network, this is obviously easy to arrange by shutting down the router/Access Point and, for that matter, your PCs if the house will be empty or before the last person goes to bed, but for small businesses it can be equally easy.
Unless an employee is working late and requires access to the WLAN, unplug it for the night—in fact, teach people how to plug it back in, just in case they do come back to the office later.
No question, cable and DSL providers emphasize the always-on capabilities of their Internet services, but there’s no reason that you have to adhere to it.
In the case of multiple access points or WLAN extenders, in office buildings, don’t hesitate to power one or more of them down, even if you don’t unplug the main router/AP/switch combinations themselves.
If you have an access point in the foyer, for example, for use primarily for guests or sales personnel to use in that area, unplug it after hours as a matter of course.
If you do power down an AP, be sure to give it a few minutes to restart when you plug it back in. The AP needs to acquire an IP address from the broadband modem, and to transmit addresses via DHCP to all the network clients.
Watch Where You Place Your APs
Like unplugging your APs, this security issue is based on common sense, not on configuration screens. APs have specific ranges beyond which the signal will not reach at all, or will reach only weakly. In an office building, place the APs as far away as possible from where you might get intruders attempting to access it.
For the most part, this means placing the APs as far from the street in front of the building as you can, unless of course you’re concerned (as you should be) with intruders driving around the back of the building and connecting from there. In that case, set the APs in the middle of the building if at all possible.
Obviously, your primary responsibility lies with ensuring that legitimate users can access the AP, but usually you have quite a bit of flexibility in this regard inside the building, especially a single-story building where beaming signals through floors and ceilings doesn’t present an issue.
Watch Your Wireless Log
In all likelihood, your AP or router/AP tracks wireless connectivity and lets you view the results in a log file. Typically, the log screen shows time of day of each connection and the IP address from which it occurred, as well as, importantly, the MAC address of that device.
In a multi-PC environment, you can use the log to determine the extent and the duration of the WLAN connections, and you can use this information to see if any unauthorized access occurred, when it occurred, and from which computer it occurred.
Although it is certainly not a detailed report, the log can provide a quick and easy way to see if access occurred at an unexpected time of day (such as the middle of the night) or from a MAC address you don’t recognize, and you can take steps accordingly to block this access.
In the former case, you can specify which types of activity you want logged, and you can tell the AP to send the log information to an e-mail address of your choice.
Unfortunately, this utility on the DI-624 isn’t sophisticated enough to enable you to set a schedule for sending the log data, nor an option for SMTP servers that require username/password authentication. Still, the feature can certainly be useful.
The Microsoft log doesn’t offer an e-mail option at all, though, so even the primitive feature of the DI-624 gets at least some points here.