Use MAC Filtering
Not only can you use the MAC addresses in static IP range restrictions, you can further increase the security on your WLAN by enabling MAC filtering on the access point.
All recent APs offer this option, typically available in a menu item or screen section labeled Filters.
Common to any network configuration, MAC filters let you specify which WLAN cards will be granted access to the wireless network, and which will not. That is, you can either allow or deny access to each MAC number.
Typically, the default configuration allows all IP addresses to gain access, and enabling the MAC filtering option lets you specify which machines can do so. You have the choice of either allowing only specific machines to have access, or of denying access to specific machines.
Obviously, the Allow method gives you stricter control, but the Deny method can be extremely useful if you want widespread access but you want to shut out a particular group of machines, permitting access to everything else.
It’s a bit like crowd control for international soccer matches: stadiums and arenas allow access to everybody except specific people or groups. Come to think of it, and to bludgeon the analogy into oblivion, these venues use both kinds of control. They allow only those with tickets, but they deny a smaller group within that larger group.
Restrict the Range of IP Numbers
As a means of making static IP numbers even more effective, configure your AP to allow only a limited range of IP addresses. This way, you control precisely how many clients can acquire an IP address, thereby lowering the chances even further of the intruder not only guessing the legal range of IP numbers, but being able to use one.
As soon as you power down one of the client PCs (or unplug the network cable), that PC’s IP number becomes available, so this system has its vulnerabilities as well, but obviously with this option in place the intruder has more work to do.
Restricting the IP range works extremely well with dynamic IP addressing as well. While not as secure as a WLAN in which each adapter has a fixed IP, a small range of dynamic IPs does make discovering the valid range at least somewhat more difficult.
Provide a range that will allow as many users to access the WLAN as necessary at any given time, and you’ve provided a useful security service. In fact, depending on how your users access the WLAN, you might need a smaller IP range than you first think.
Unless all users access the WLAN at the same time, you can restrict the range of dynamic IPs to a number smaller than the total number of users, because as soon as one user disconnects, either by powering down the PC or removing the WLAN adapter, that IP number becomes available for use.
In the case of static IP addresses, here too you can reuse IP numbers. As users leave their workstations for an extended period of time, you can disable that PC’s connection (in the Network Connections window) and have another PC use that static IP.
This method takes reliable management skills because if you have two PCs configured with the same IP address, you’ll get a network error, but it’s certainly possible.
In a small office, for example if you have four PCs, only two of which need to access the network at a time, you can configure your AP for a two-number dynamic IP range, or you can configure it to use only two fixed IP numbers. Either way, you significantly lower the chance of intrusion.
Change the Names of Additional Access Points
When you add additional access points to your system, each one adds the same vulnerabilities as the original. You can complete every security configuration possible on the original access point. But the minute you add another, you open up the possibility of people easily connecting to it, and through it, to the primary access point.
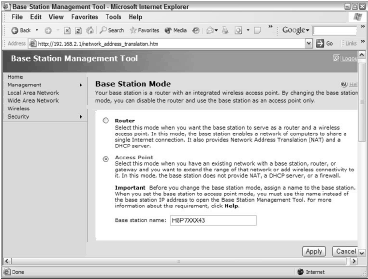
It’s a bit like pinning a note to your front door to remind yourself of the hiding place for the door key and the access code for the burglar alarm system. For this tip, we use the Microsoft MN-700 Base Station as the example.
As Figure 1 shows, you can change the base station to access point mode, in which the device no longer acts as a router and no longer connects directly to the cable or DSL modem.
Instead, it becomes simply another network device on you wired LAN, but unlike the other PCs on the network, this device provides wireless service. If you already have an existing LAN, adding this device in access point mode gives you an infrastructure LAN.
But if an AP is already in place, as is the case if you connect the MN-700 to an existing MN-700 or another AP/router, the new AP provides a second wireless LAN, complete with all the possible security issues of any other AP with its factory settings established.
From a security standpoint, you provide the first round of security by giving the new AP a new name. Any name will do, but once again, try to make it something an intruder won’t easily guess.
This particular product uses MN-700 as its default name, and obviously anyone seriously interested in breaking into your WLAN will know the industry defaults. Give it a new, unique name, to shut the door as much as possible.