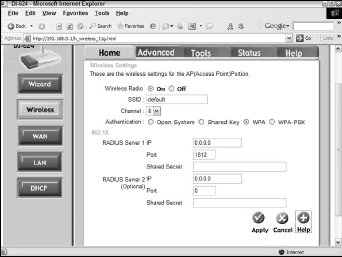
As with your WEP-enabled network, configure your access point first, so that you can simply configure all the network clients afterwards with the AP up and running. Figure 1 shows the relevant configuration screen on the D-Link DI-624 configuration screens.
Note that the D-Link supports both the normal and the shared key modes of WPA. Most APs manufactured in the past year or so offer support for both, and as long as your WLAN adapters support these modes, you can use whichever you prefer.
Well, not exactly. To use WPA rather than WPA-PSK, you need a RADIUS server, so unless you have one of these devices, you have no real choice but to choose the PSK version.
For the sake of this tutorial and its intended audience, we stick with WPA-PSK for the demonstrations, but where discussions of RADIUS-based WPA seem applicable, we continue to refer to that technology as well.
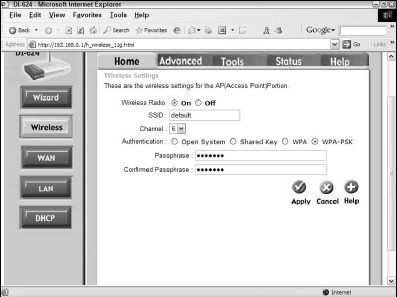
To see the difference, look at Figure 2 in conjunction with Figure 1.
Figure 1 shows an areas for 802.11 configuration, in which you must specify the IP address, the port, and the shared secret key of at least one, and possibly two, RADIUS servers. Without a RADIUS server operating, you obviously can’t do so.
Figure 2, by contrast, shows the WPA-SPK option in place. Here, you have only two fields below the Authentication line that you can complete: Passphrase and Confirm Passphrase. Here, as you probably expect by the format, you simply type the passphrase (also called the Shared Secret) under which you want WPA-SPK to operate.
As you’ll see in a minute, you must enter the same passphrase in the configuration dialog boxes of each node on the network to allow WPA security—and, indeed, to allow any form of wireless data transfer, because once WPA-SPK has been established on the AP, no WLAN adapter can connect without conforming to the AP’s security requirements.
As with every other password or passphrase you have on your computer system, make this one as secure as possible to make intrusion as difficult as possible.
In fact, because the WLAN adapters happily store the passwords for you, provide a password that’s almost impossible to memorize, precisely because you have to type it only once on each machine.
Yes, you’ll want to change the password periodically, but WPA-SPK does tend to be harder to crack than WEP. So as long as you perform a periodic passphrase update, say once a month for a home network and once a week for a small office network, you should be reasonably safe.
Of course, you can change the passphrase daily for even greater effect, as long as you remember to change it on each network client PC as well. In this way, the WPA-SPK passphrase resembles the Encryption Key in WEP, the effectiveness of which increases dramatically the more often you change it.
The passphrase must contain between 8 and 63 characters.