WPA represents a stepping stone between the limited security capabilities of WEP and the projected “real” security of the upcoming IEEE protocol called 802.11i, also known (adding to the confusion) as WPA 2. WPA exists, and works reasonably well, while 802.11i remains a technology around the corner.
In other words, it’s not yet a solution, although you can expect it to appear, in force, in products in late 2004 or early 2005. In the meantime, WPA has captured the interest of security-minded IT professionals and even some home and small office users.
Primarily because their existing equipment already includes it or—and this is extremely important—they can upgrade the firmware of their existing equipment to get it. By contrast, when 802.11i hits the market, you will almost certainly need to purchase new APs and WLAN adapters to take advantage of it.
Practically speaking, this means WEP and WPA will continue to secure WLANs for quite some time to come because homes, small offices, and even some larger companies won’t immediately spring for new equipment. As with all security expenditures, the return on investment is nearly impossible to prove because security acts as a preventative.
And the only way to believe in the effectiveness of preventatives is to be convinced that whatever they were preventing would have happened in the first place. Obviously, you can’t predict anything of the kind, so justifying the cost becomes difficult. In the meantime, then, you have WEP and WPA.
WPA and 802.11i
If Wi-Fi Protected Access provides a stepping stone to the more secure 802.11i (WPA 2), what sort of stepping stone is it? The answer to this question begins with the answer to another question: How is WPA different from WEP?
As discussed briefly, the primary disadvantage with WEP lies with its fixed security keys. Once they are set, WEP administrators can change them, but in many typical WEP installations the keys simply don’t get changed, and the protocol, with its lack of built-in ability to cycle through keys on a periodic basis, doesn’t help things.
As a result of this problem, WEP security is breachable and breakable, to the degree that home networks can end up sharing Internet connections and other resources (such as files) with intruders, and company networks can become seriously compromised.
WEP is unquestionably better than nothing, but for networks with a lot to lose, better than nothing hardly fills the bill. The 802.11i protocol addresses these and other security issues in depth, where WPA addressed them only to a degree.
WPA begins by improving WEP’s implementation of the RSA Security RC4 encryption technology, specifically the size of the initialization vector, which resides in the first bytes of data and begins the process of recognizing the key shared by the sending and receiving devices.
WEP uses a 24-bit initialization vector early in the process of a network transmission; in WPA, this vector increases to 48 bits. As with all encryption technologies, increasing the size even a small amount increases the difficulty of cracking the encryption almost exponentially, so a doubling from 24 bits to 48 bits renders the initialization vector far, far harder to crack.
Right from the start of the data transmission process, therefore, WPA shows its enhanced strength. Among WPA’s most prominent additions, Temporal Key Integrity Protocol (TKIP) provides the greatest security for individual data packets, the small “chunks” of data into which networking protocols divide your messages before sending.
TKIP mixes keys on a packet-by-packet basis, changes these keys automatically and regularly, and verifies the security configuration with each change.
These key changes are crucial to the security capabilities of WPA and 802.11i both, and make up for the inability of earlier 802.11 implementations (including 11a, 11b, and 11g) to change the encryption key for some transmission types.
WPA mandates rekeying the case of all transmissions, with TKIP providing the frame by frame rekeying, and WPA itself providing the mechanism by which the AP communicates the changed keys to the adapters.
In addition, TKIP provides a means of checking the integrity of the message, a technology known as Message Integrity Checking (MIC) (but often referred to as Michael), that blocks intruders from adding small bits of data to a packet to calculate the encryption key (which is a problem with WEP).
TKIP is therefore a part of WPA’s overall key management feature, and the two together eliminate the problem of static encryption keys that renders WEP so vulnerable. Authentication, an especially weak component of WEP, also undergoes a significant upgrade with WPA.
First of all, you can no longer configure your WLAN to operate without authentication encryption, as you can with WEP. In addition, WPA authentication is based on the Extensible Authentication Protocol (EAP), a secured extension to the Internet’s long-lived Point-to-Point Protocol (PPP), and a core element of 802.11i as well.
EAP handles digital certificates, secure IDs, and other authentication elements in the security world, and does its job in part by preventing connection to the WLAN by rogue APs and adapters.
Furthermore, WPA supports the technology known as preshared key authentication, an option in WPA equipment configuration abbreviated to WPA-PSK. In this configuration, the AP and the adapters share a predetermined key, with the sharing itself password-protected.
When the AP determines that the passwords match, the adapter can gain access to the network. This system simplifies the user-specific credentials required in WPA itself, and eliminates the need, in smaller networks, for a special server to handle authentication requests.
Even so, PSK technology is more readily breached than straight WPA, so use it only for the sake of ease of use. Put another way, it’s better than WEP, but not as good as WPA on its own.
Despite these changes, however, TKIP operates perfectly well with existing wireless devices; as long as you add WPA capabilities to your APs and WLAN adapters, you don’t need to run out and buy new equipment.
Such is not the case with 802.11i, which as we write this looks as if it will require new hardware to incorporate its significantly stronger security features. If you want high security, you’re going to have to pay for it. 802.11i extends the improvements in WPA even further.
Perhaps the most important single addition is the addition of the Advanced Encryption Standard (AES), a block cipher technology already available with some implementations of WPA, but not mandatory because it often requires new hardware to perform effectively.
A U.S. government standard authorized by the National Institute of Standards and Technology (NIST), AES enables security among WLAN nodes operating in both ad hoc and infrastructure mode.
AES encryption can use key sizes up to 256-bits, possible today with even some proprietary modifications of WEP but, when combined with WPA’s other improvements, an even greater improvement to what we have now.
AES encryption is simply one part of 802.11i’s Robust Security Network, which of course abbreviates to RSN (nobody in the computer world actually spells any term out, as you’ll see in the next sentence).
Combining 802.11 itself, along with EAP and AES, RSN provides a method of dynamic authentication and encryption designed to eliminate both the security problems and the performance downgrades currently experienced with both WEP and WPA.
RSN replaces TKIP’s constantly rotating encryption keys with the more secure AES implementation, and requires a Remote Authentication Dial-In User Service (RADIUS) server to provide full authentication.
For this reason, 802.11i will be found primarily in larger businesses and organizations, with home and small office APs providing, quite probably, a less comprehensive version of RADIUS.
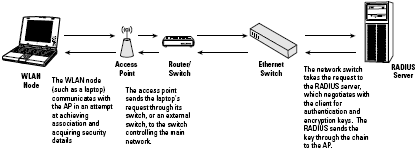
Figure below shows a typical diagram of the data flow for a full 802.11i implementation.
In this process, the WLAN user (from a laptop, say) performs some network activity. The laptop’s WLAN adapter sends a request for association and security to the AP.
The AP forwards the request through the switch to the RADIUS server, which performs the authentication, thereby allowing the switch and the laptop to create the necessary encryption key for that session.
The switch encrypts the key with AES and sends it back through the access point to the laptop, and the WLAN adapter, configured for 802.11i, now encrypts all signals for this session with this key.
As the laptop makes new requests, a new authentication and key creation process begins, and this same process, with different encryption results, occurs with each client on the network.