One of the most interesting ways to protect your resources from wireless intrusion is to do the unexpected and invite the intruders inside. Still relatively new in the world of security, honeypots have acquired a kind of cult following, as well as a practical usefulness, precisely because what they do seems both obvious and strange.
In effect, a honeypot litters the airwaves with simulated access points, inviting intruders to take advantage of the network but, in simple cases at least, offering them nowhere to go.
Instead of trying to hide your real AP by engaging all the other security mechanisms, you put it out in the open with a crowd of other APs, hiding the real one simply by giving the intruder too much to do. They might never know which is the real AP. A true honeypot, in fact, has a purpose different from simply disguising the real Access Point.
Administrators design them to monitor and study what hackers do and how to defeat their attempts at unauthorized access. In fact, at least one group of researchers has banded together for the sake of creating honeypot-like environments to catch intruders and learn their methods.
The Honeynet Project has a four-phase process in the works to develop ever more sophisticated ways of luring intruders in and studying their behavior, and has even developed a bootable CD-ROM that automatically establishes a Honeynet gateway for your network.
Called the Honeywall, the CD-ROM creates a system that hackers can target as they wish, while the system monitors and records their actions. However, and indeed for most users, the honeypot has value for its ability to deceive intruders rather than capture them.
In all likelihood, you simply want people to stay away from your valuable resources—your files, your Internet access, and so on—and you have less concern for who attempts to gain access and with what tools and methods.
Let’s proceed with that assumption. While an organizational-level honeypot requires multiple computer and multiple access points, you can create a small virtual honeypot using several different tools. And what exactly is a virtual honeypot?
A real honeypot requires real computers running real operating systems and holding real and frequently changed data—in other words, it’s a front, designed to draw the intruder inside and keep him occupied by making him think it’s the real thing.
By contrast, a virtual honeypot offers numerous false fronts to the intruder, with the goal of simply having him lose interest in trying to locate the real resource.
In the Linux world, one of the better known honeypot utilities is Black Alchemy’s Fake AP, which automatically generates several thousand simulated access points in an attempt to confuse would-be intruders. For Windows users, a program such as Honeyd-WIN32 creates fake APs while simultaneously simulating multiple operating systems.
Despite the usefulness of honeypots, however, keep in mind one interesting and important point: legalities. Luring a hacker into a honeypot could be interpreted as entrapment, and you could be liable.
To date, the matter remains untested in court, but you can rest assured that someone, somewhere, will make the claim someday. And as you’ve come to know with other computer matters, it’s almost impossible to predict which way the electronic wind will blow.
To get an idea of how virtual honeypots work, this tutorial examines KF Sensor, which bills itself as a honeypot-based Intrusion Detection System (IDS). It functions by simulating the ports that make Windows PCs vulnerable to attacks.
KF Sensor simulates system services on the application layer of the OSI Network Model, which means, in effect, that it will look like any other server on the network, making simulated use of Windows security technologies.
The idea, indeed, is to run KF Sensor on a separate PC entirely, alongside other servers, but you can run it on user machines instead, obviously a more realistic situation on a small network.
KF Sensor lets your target PC operate in two modes: Sim Banner and Sim Standard Server. Sim Banner offers a basic server emulation, sending a small piece of data that lets the visitor (KF Sensor’s term for any intruder, including Trojan horses and viruses) think it’s a legitimate server.
Sim Standard Server provides a much more sophisticated emulation, enabling you to configure your server as a fake FTP, HTTP, POP3, SMTP, SQL, Terminal server, and more.
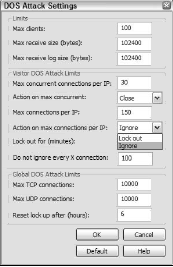
You can also minimize the number of connections and log file size in an effort to fend off Denial of Service (DOS) attacks, intrusions that make a huge number of near-simultaneous requests to a server in order to overwhelm it and thus bring it down. Figure 1 shows the DOS Attack Settings dialog box.
 After installing KF Sensor and rebooting Windows, the Setup Wizard opens automatically. Your first choice is to decide which components to add, with each component offering a different potential target.
After installing KF Sensor and rebooting Windows, the Setup Wizard opens automatically. Your first choice is to decide which components to add, with each component offering a different potential target.
These range from NetBIOS through Trojans, Universal Plug and Play, and a variety of standard services, and unless you have a reason to exclude specific services—for example, if you’re attempting to trap intruders attempting one or two attack types—leave the default.
The next stage of the wizard asks you if you want to install the program as a system service; in Windows NT, 2000, or XP, a system service runs on launch, continuing to run no matter which user logs in.
For the most part, only systems administrators want to experiment with luring attackers, so don’t install as a systems service unless you plan to use this particular computer as a central target. With KF Sensor installed, you can set to work luring and monitoring intrusions.
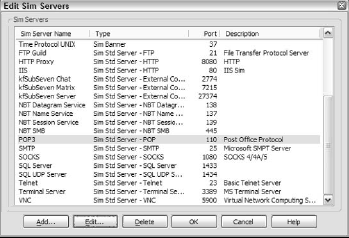
Figure 2 shows the Edit Sim Servers dialog box, one of several Edit dialog boxes offered in the KF Sensor interface.
This figure shows the default configuration of the servers simulated when installing KF Sensor, with a variety of Banner Servers not visible above the list. This list offers typical settings for these servers, but you can edit any of them to specify your own configuration.
To make KF Sensor as flexible as possible for any implementation, you can build scenarios with differing simulated servers in each. The default scenario, includes a wide range of possible intrusions, and functions as a kind of Swiss Army knife for catching intrusions.
However, you can edit any of these settings to tailor each component to the port number and protocol expected from that particular intrusion, and to establish the severity of the intrusion type and the action you want KF Sensor to perform on intrusion.
The range of possibilities is almost limitless, and to understand them all you need a studied awareness of what these intrusions do. Some of the listed items represent Trojans and other malicious programs, but others, such as PC Anywhere, refer to perfectly legitimate programs designed to access your PC, but which can be used by would-be intruders.
Indeed, one of the more fascinating results of studying a program such as KF Sensor is the amount you can learn about the sheer possibility of intrusion, and the extent to which intruders will go to break into your system.