Use Virtual Servers
All routers manufactured today have a virtual server feature, one that gives you control over precisely which network services the router/Access Point will allow network users to access. Usually this feature defaults to disabled, so you needn’t worry about configuring it unless you have a specific reason to do so.
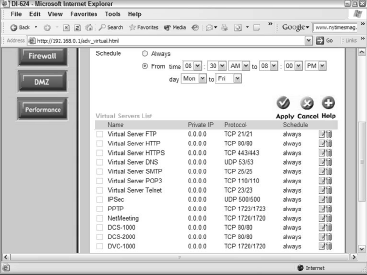
But once you enable the virtual servers for any purpose, monitor the feature closely to ensure that you don’t open your network to unwanted access. Figure 1 shows the virtual server feature available on the D-Link DI-624.
In each case, you can configure and edit the local, private IP number dedicated to that specific network service, and you can schedule the times during which that service is accessible.
Scheduling, in fact, works very well as a deterrent for intrusion; as with anything else related to networks, don’t have something turned on if nobody needs to use it at that time.
As Figure 1 shows, the DI-624 configuration screen offers several typical server functions:
- FTP—File Transfer Protocol (old-style but fast data transfer)
- HTTP—HyperText Transfer Protocol (that is, the Web)
- HTTPS—Secure Web services (using encryption)
- DNS—Domain Name System (conversion of user-friendly addresses into IP numbers)
- SMTP—Simple Mail Transfer Protocol (standard for sending e-mail)
- POP3—Post Office Protocol version 3 (standard for receiving e-mail)
- Telnet—Accessing Windows NT/2000/XP machines via a command line
- IPSec—IP Security—security mechanism used on Virtual Private Networks
- NetMeeting—Allows remote users to use NetMeeting with one another through the local network
- Other D-Link products such as Internet cameras
Without enabling these items, your router will not admit traffic for these protocols. If you want to run an intranet Web server from behind your local network, for example, you need to enable it, although you can help your security issue by specifying a different port than the standard for that protocol.
For example, configuring the router/AP to use port 8080 for Internet access, instead of the standard port 80, or to use port 26 for SMTP service, instead of the standard port 25, can significantly reduce the danger of intrusion (although you should change these ports regularly as well).
Note that these changes affect all network activities, not only those involving WLAN users. But their importance for security is such that even when setup a WLAN, they become significant.
When you configure a server at the router level, you need to configure all network clients, including those connected through your AP, to access the correct port.